Unlock log analytics: Seamless insights without writing queries
Dynatrace
MAY 28, 2024
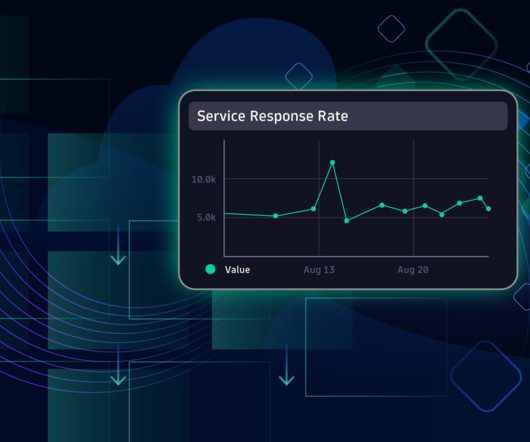
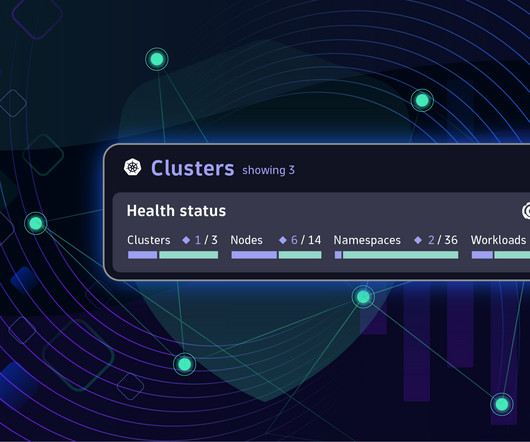
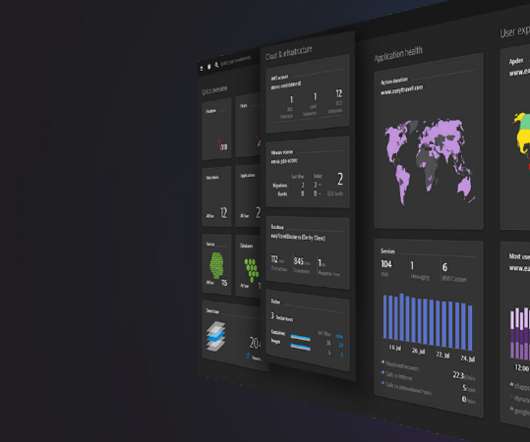
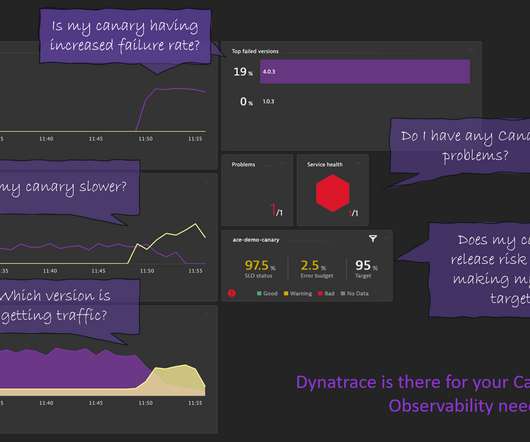
Logs provide answers, but monitoring is a challenge Manual tagging is error-prone Making sure your required logs are monitored is a task distributed between the data owner and the monitoring administrator. Often, it comes down to provisioning YAML configuration files and listing the files or log sources required for monitoring.






































Let's personalize your content