Open Source Software Security: Is Open Source Software Safe?
Percona
APRIL 26, 2023
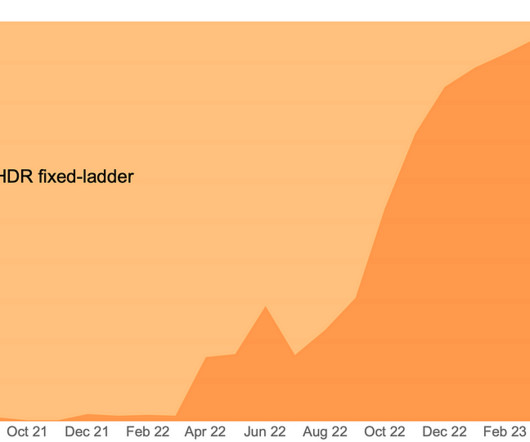
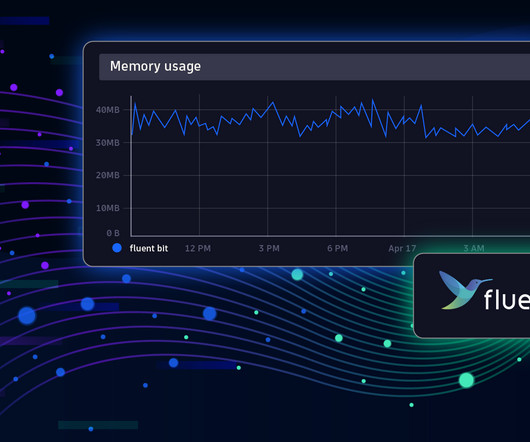
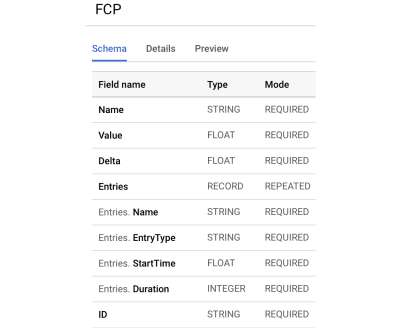
Even though open source software is firmly in the mainstream, used widely by businesses, governments, and everyone who owns a cell phone or computer, the question repeatedly arises: “Is open source software safe?” Is open source software as stable as other software? Our bar is higher than that.

































Let's personalize your content