Observability platform vs. observability tools
Dynatrace
DECEMBER 22, 2021
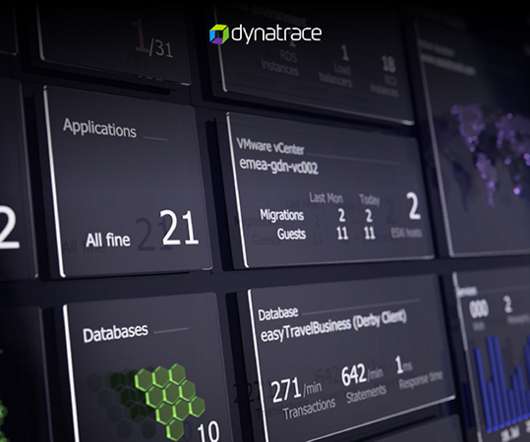
As a result, teams can gain full visibility into their applications and multicloud infrastructure. For example, in 2005, Dynatrace introduced a distributed tracing tool that allowed developers to implement local tracing and debugging. This helps teams to easily solve problems as, or even before, they occur.











Let's personalize your content